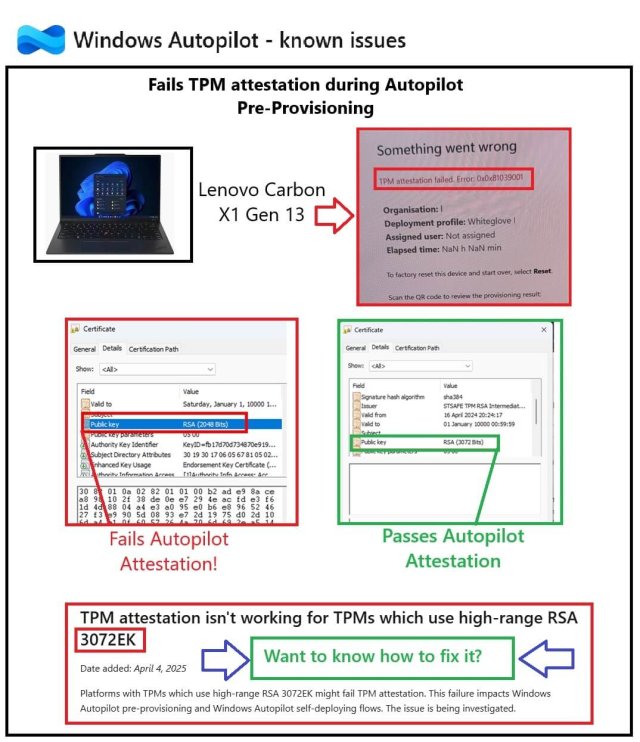
Threat actors are constantly lurking in the shadows, waiting to exploit vulnerabilities in our digital world and make our lives, as sys admins miserable. We thought it might be prudent to give our own spin on the Critical Vulnerability and Exposure (CVE) 0-day exploit that has been discovered in the wild recently. If you read the headlines and the CVE description over at NIST, you might be led to believe that the exploit only affects Google Chrome. But the libwebp library is used across many apps. The attack surface is broad, the criticality is, well, critical. So what’s the actual scoop?
CVE-2023-5129 – A Google Chrome problem?
There has been a lot of noise about CVE-2023-5129 recently, so which of the multiple CVE IDs should we be focusing on here? Is it only Google Chrome affected by the vulnerability? When we take a look at the NIST website for CVE-2023-5129, we can see it has actually been rejected.
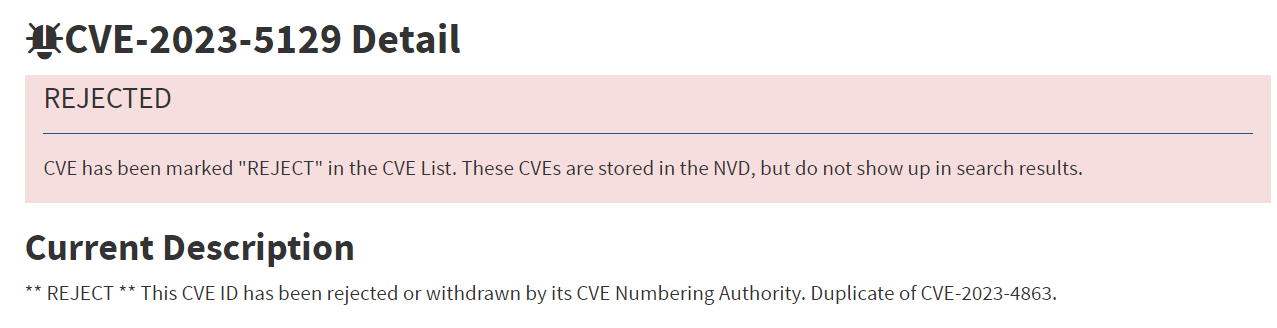
We don’t really know the intent behind the submission for CVE-2023-5129 but out best guess is that Google were trying to highlight that the open source libwebp library security vulnerability affected more than just Google Chrome – and they are right.
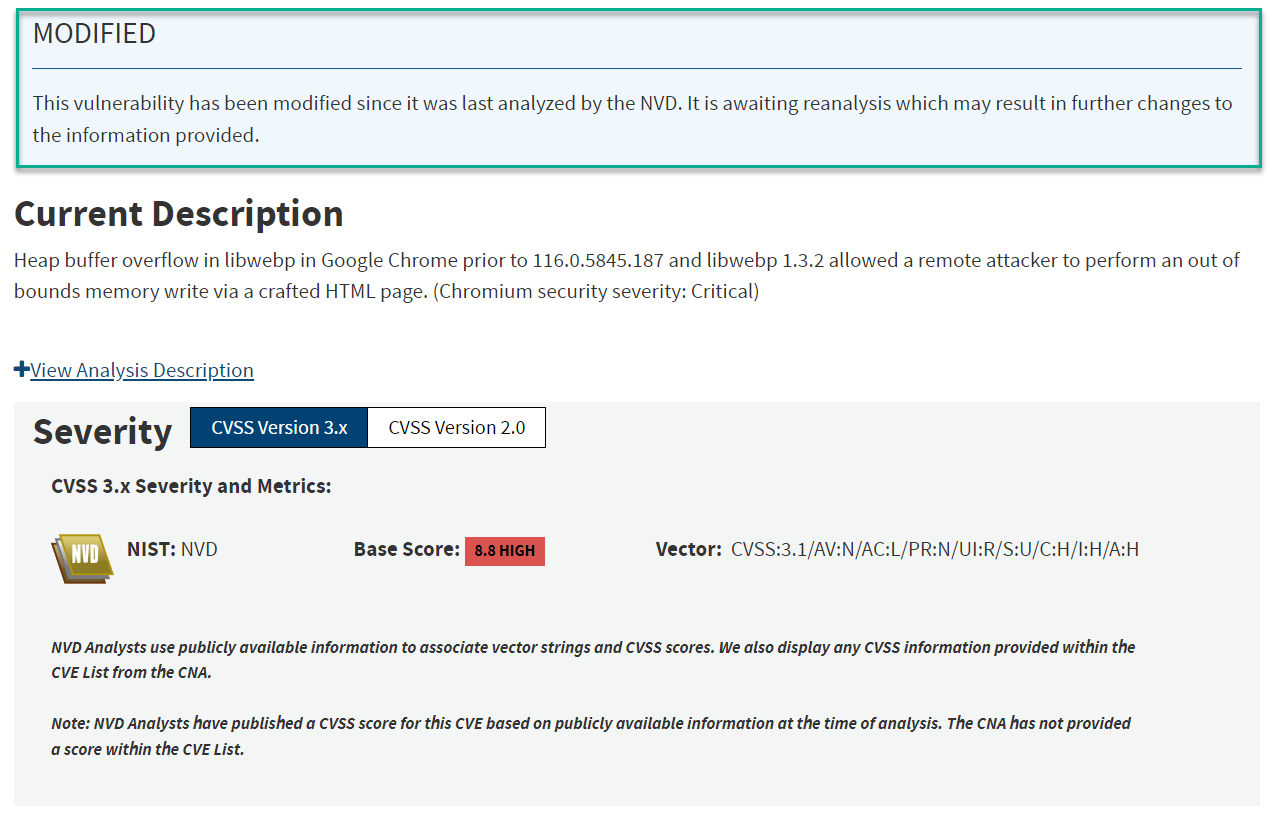
We can see that CVE-2023-4863 has been modified – the hunch is the vulnerability will draw less attention to a single product and more to the fact that the problem is wider spread – and you should patch all your things.
Ground Zero – A Quick peek at Apple Security Engineering
On 7th September 2023, the good folks at Citizen Lab published details about a zero day exploit coined BLASTPASS (seriousness aside, what a cool name for an exploit). Multiple apple OS products were affected. Apple security engineering was quick to released updates to address the arbitrary code execution vulnerability. Specifically, they were addressing CVE-2023-41064 and CVE-2023-41061 which were addressed in:-
iOS 16.6.1
iPadOS 16.6.1
macOS Monterey 12.6.9
macOS Ventura 13.5.2
iOS 15.7.9
iPadOS 15.7.9
macOS Big Sur 11.7.10
Note: If you are looking for a neat site to pin, Citizen lab have some great articles you should check out at https://citizenlab.ca/
Heap Buffer Overflow
The libwebp security vulnerability is located within a specific part of the open-source libwebp library, which is responsible for both encoding and decoding images in the WebP format. More precisely, this vulnerability involves a problem known as a heap buffer overflow, occurring within the libwebp library’s implementation of the Huffman coding algorithm.
Huffman coding is a crucial technique employed to achieve lossless compression when working with WebP images. The recently discovered heap buffer overflow vulnerability allows for unauthorized and potentially malicious overflow of data in a specific memory storage area known as the “heap”, which is utilized during the Huffman coding process.
This vulnerability poses a significant security risk as it could be exploited to manipulate and compromise the integrity of images in WebP format, potentially leading to unauthorized access or the execution of malicious code, in maliciously crafted html pages, for commonly used apps like, but not restricted to, Electron, Chromium based browsers (including Microsoft Edge), Mozilla Firefox and more.
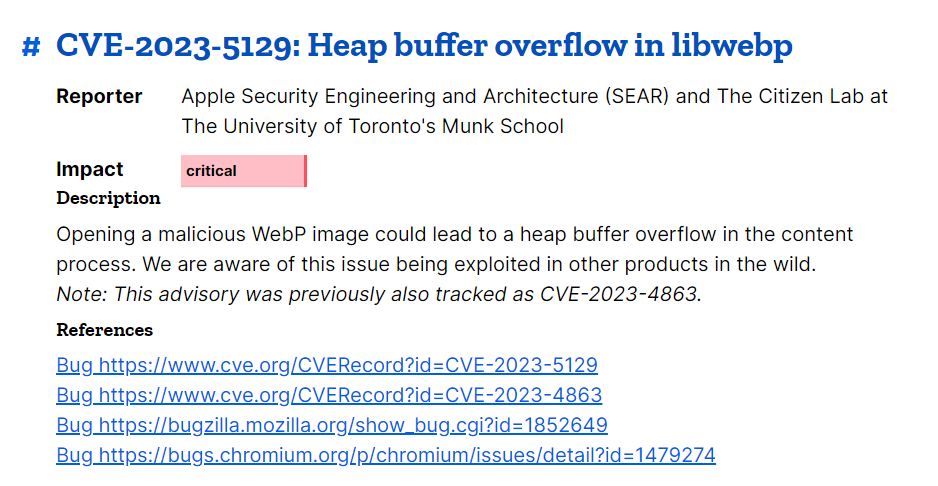
CVE-2023-4863
The focus is back on CVE-2023-4863, for now. Over at Mitre, we get an idea of other vendors who have released updates to address the zero day libwebp vulnerability. Some vendors are still listing CVE-2023-5129 as the vulnerability that was fixed, we can overlook the error of their ways, for now at least. Remember, this isn’t just a vulnerability that affects Google Chrome. As an example, Mozilla Firefox has been updated to protect against any potential malicious webp image:-
What should I patch?
You are asking the question to a bunch of people who are passionate about patching everything. Even the sleeves of Grandpa’s jumper. Nobody likes to hear the term “Arbitrary code execution” or “state sponsored threat actors” when eating dinner. Save yourselves the conversation at the next team meeting and casually lean back in your chair and announce “We got it covered”.
We have seen vendors release patches, they are already in the Patch My PC catalog. A few examples with the vulnerability patched are include:-
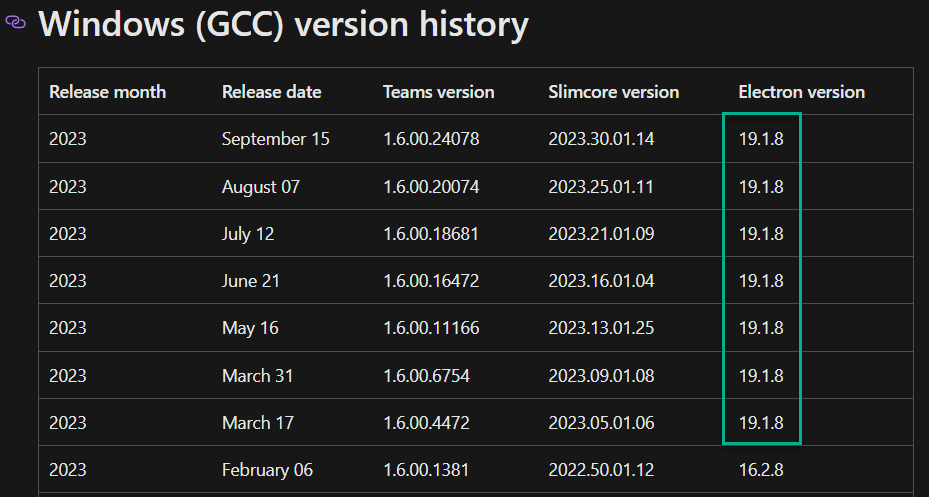
Microsoft Teams is an interesting one. The latest version, 1.6.00.24078, still lists that it uses Electron 19.1.8. This version of Electron has been around for a while – has it been patched? No evidence suggests that it has. We need to do some more digging in to this one.
Summary
It is so difficult to stay on top of these CVE’s, more so for SME’s how maybe don’t have a dedicated security team to track and remediate devices. The webp image format allows websites to display high-quality images with much smaller file sizes than traditional formats such as JPG. It is used extensively in more apps than you would probably know. You really have to have your eye on the ball in this game.
We are a few cycles of the sun away from having a “1 button to save us all from the zero day” feature in our arsenal. Until then, patch everything, all the time, but don’t let it be costly on your time or your health. We got you covered!