- kbupdate – a community Windows PowerShell module written by Chrissie LeMaire (SQL & PS MVP, GitHub Star, creator of dbatools)
- wsusscn2.cab – a Microsoft Windows update offline file, regularly updated by Microsoft every Patch Tuesday
Why use PowerShell to Install Updates?
There is no shortage of patching solutions to manage Windows updates out there. However, orchestrating your own patching routines with code allows you to create a bespoke patching solution.
For example, you might have a complicated application server topology involving multiple Windows server hosts running a variety of services. Perhaps they need to shutdown/startup in a specific order or require custom pre/post actions for each step during your patching routine.
Tools do exist on the market that offer the flexibility to manage updates without code. However, to codify Windows update with PowerShell opens the door to limitless patching. You could use cloud services such as Azure Automation and Azure Arc to orchestrate these complex patching routines for your on-premises servers, too.
On the other hand, you might be a small business or have a small budget and can’t afford to buy such tools to patch just your endpoints. For this, you use Windows Task Scheduler to configure kbupdate to install only specific types of updates. This will give you more granular control of automatic updates using PowerShell code.
Manage Windows Update with kbupdate
kbupdate is a PowerShell module that can find, install, and uninstall Windows updates. One of its greatest features is that it can report what updates are missing on a Windows host that are not approved in a Windows Server Update Service (WSUS) server or any other Windows update patching solution.
Be sure to check out this YouTube recording from a live demo of kbupdate given by Chrissie at PsConfEU 2022 MiniCon!
At the time of writing this, kbupdate supports both Windows PowerShell 5.1 and PowerShell 7.2.
Before you start using kbupdate
Depending on your version of PowerShell, or if you are running an older Windows version than Windows 10 or Windows Server 2016, make sure you update to the latest Windows Management Framework 5.1 – Windows Management Framework (WMF) – PowerShell | Microsoft Learn.
Run the below in the PowerShell console to install the latest version of kbupdate from the PowerShell Gallery:
Install-Module kbupdate -Scope CurrentUser
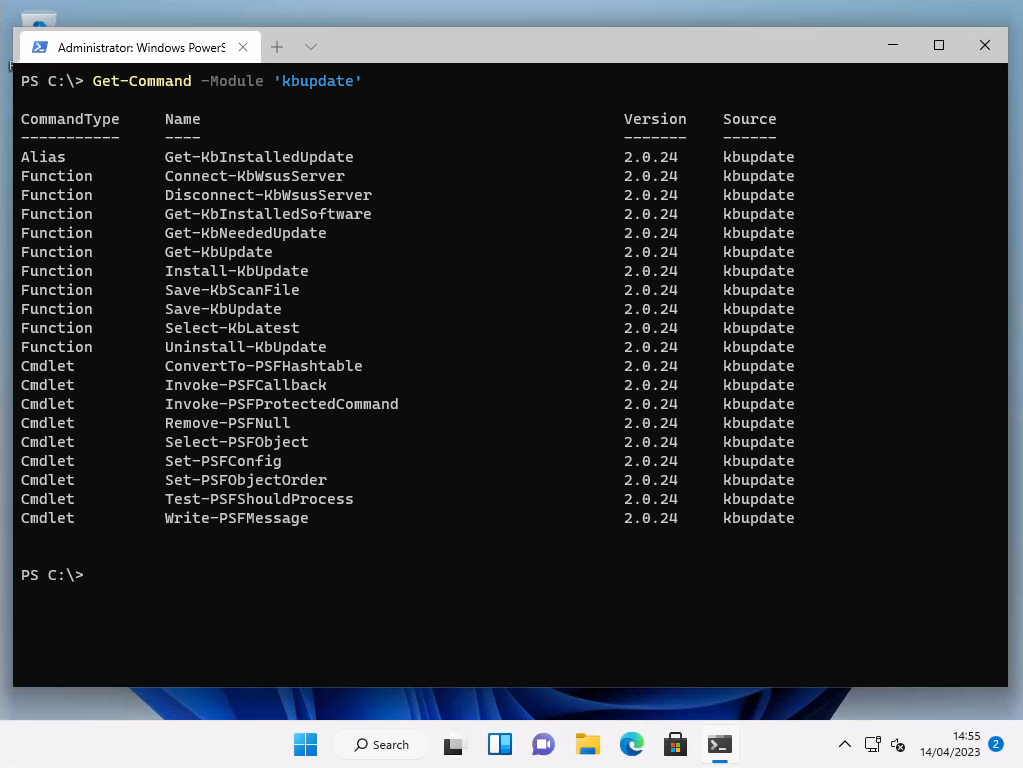
Get-Command -Module 'kbupdate'Also, use the below to see all the help information for a specific function:
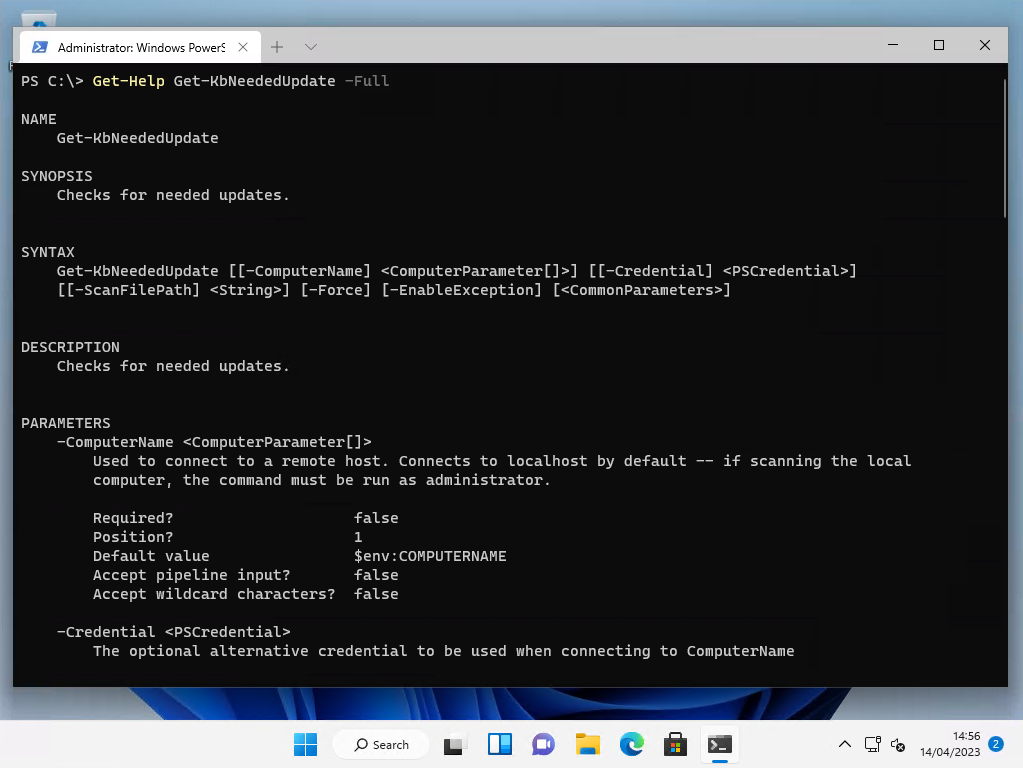
Get-Help Get-KbNeededUpdate -Full
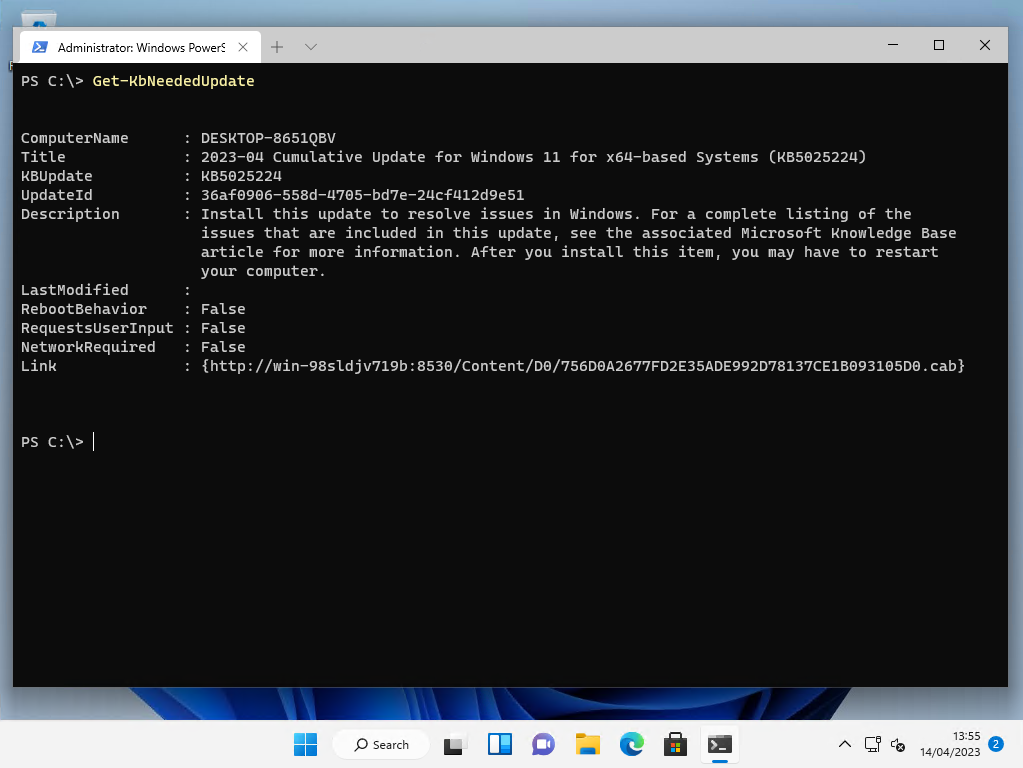
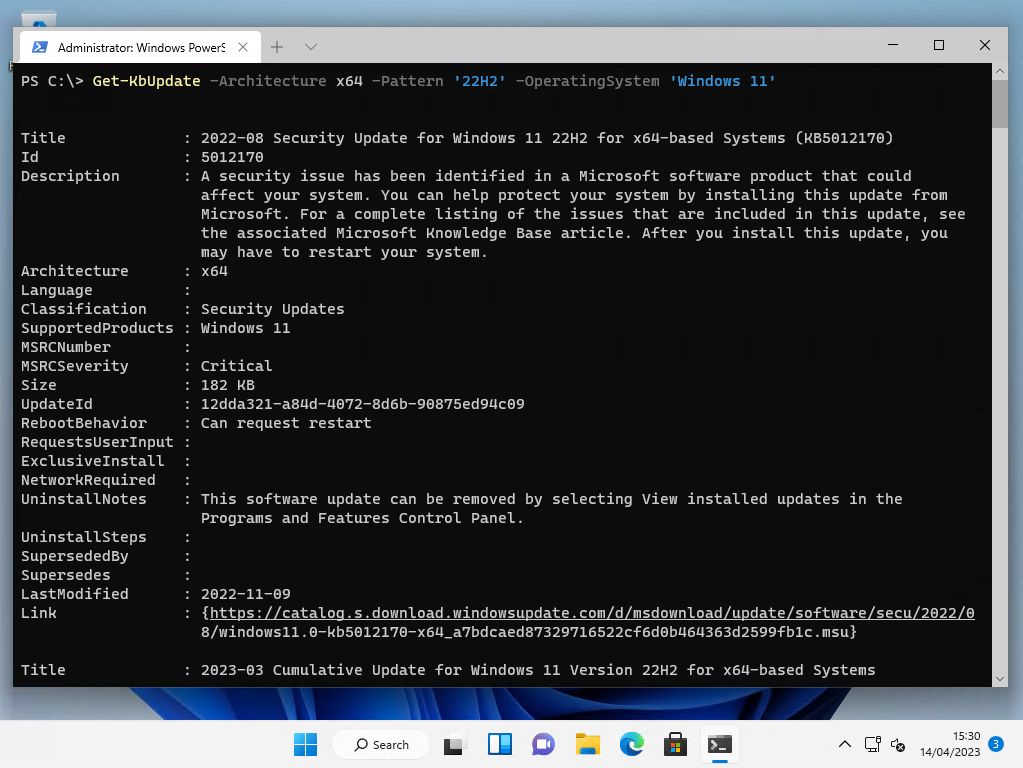
Get-KbNeededUpdate
Get-KbNeededUpdateThis code can take a while to run, especially if there are many updates to search through.
By default, if your Windows Update Agent is configured to report to a WSUS server, then it will scan against approved updates in WSUS. Otherwise, it will scan against Windows Update (aka the Microsoft update servers.)
If you want to forcefully scan against Windows Update, and not WSUS, use the -UseWindowsUpdate parameter.
Get-KbNeededUpdate -UseWindowsUpdateNOTE: If running this command on an unpatched Windows 10 or 11 device to scan against your WSUS server, and:
- the Windows 10 or 11 category is not enabled in WSUS, or
- no Windows 10 or 11 updates are approved
Get-KbNeededUpdate will not show you any available updates.
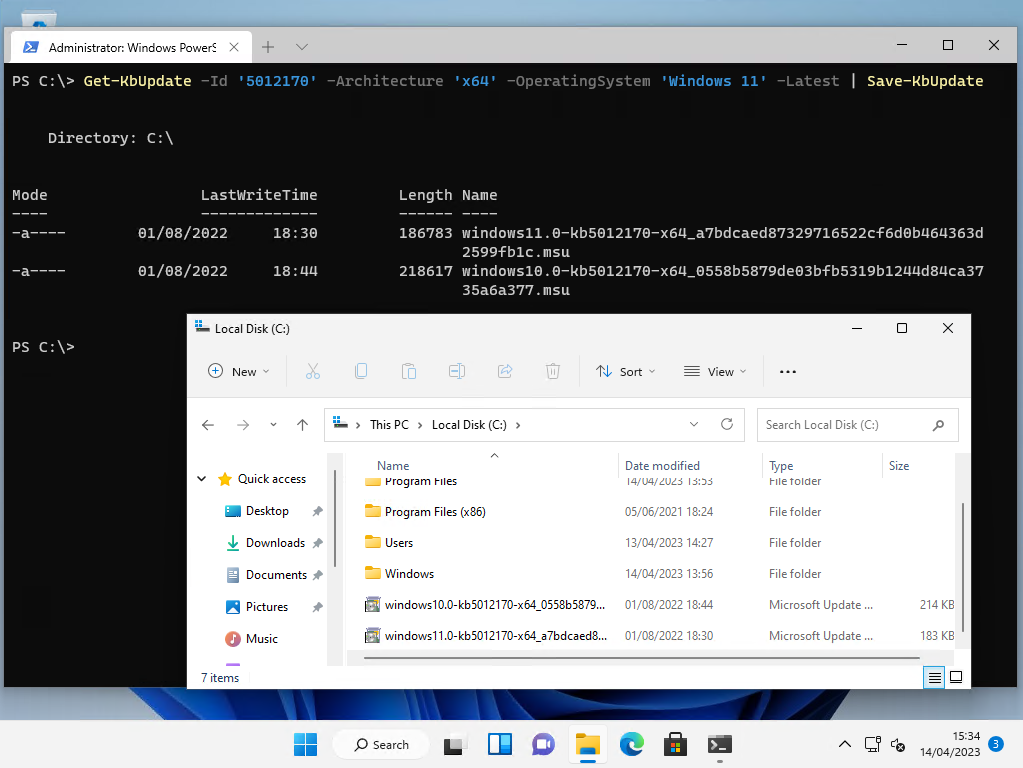
Install-KbUpdate
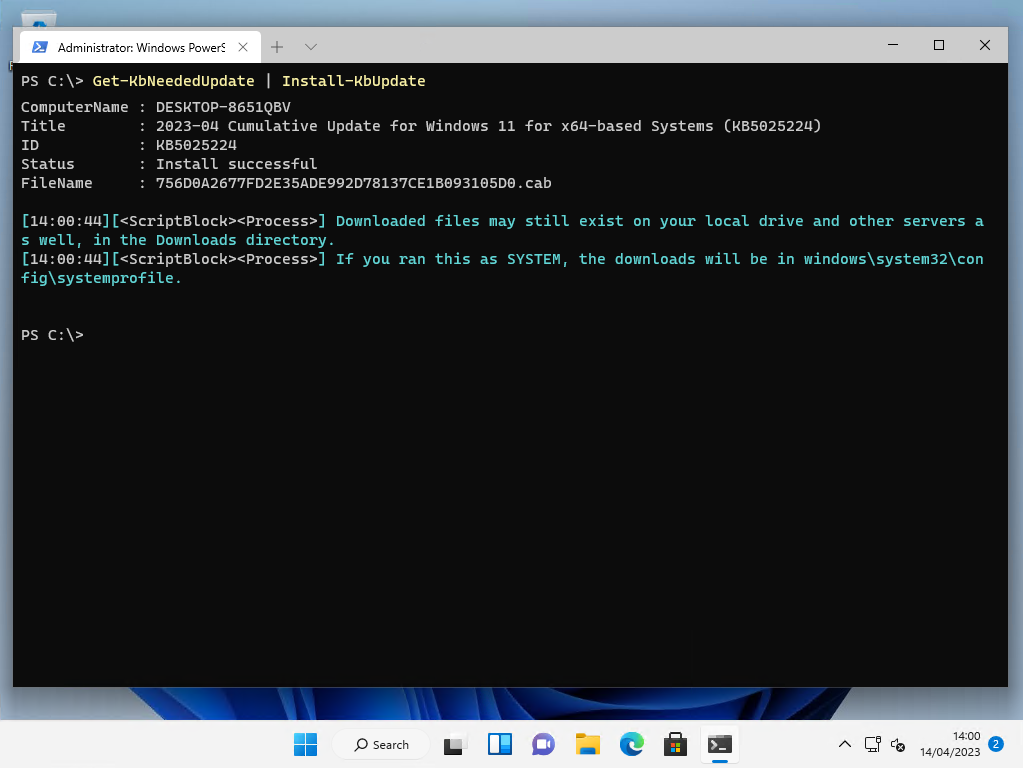
Install-KbUpdate can be used in a variety of ways to install updates, but we’ll leverage the pipeline system of PowerShell by simply supplying the output from Get-KbNeededUpdate, straight into Install-KbUpdate, so we can automatically download and install all needed updates:
Get-KbNeededUpdate | Install-KbUpdate
Get-KbUpdate
Save-KbUpdate
Remote Computers
Reporting the Absolute Truth for Windows Update Compliance using PowerShell
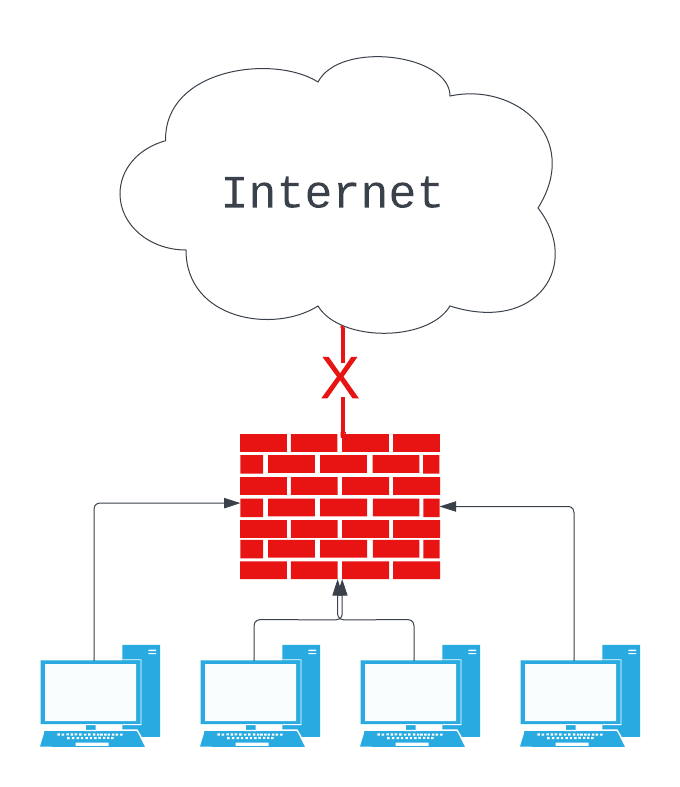
Windows Update Offline Scan File – wsusscn2.cab
Developers generally use the offline cab file so they can programmatically identify missing updates against a Windows system without access to WSUS, Configuration Manager, or Windows Update.
Microsoft provides two code examples written in VBScript:
- Using WUA to Scan for Updates Offline – Win32 apps | Microsoft Learn
- Searching, Downloading, and Installing Updates – Win32 apps | Microsoft Learn
Here is a simplified working example of the same using Windows PowerShell:
# Download the wsusscn2.cab file from the Microsoft Update Catalog
$Url = 'https://catalog.s.download.windowsupdate.com/microsoftupdate/v6/wsusscan/wsusscn2.cab'
$ScanFile = '{0}\wsusscn2.cab' -f $env:temp
[System.Net.WebClient]::new().DownloadFile($Url, $ScanFile)
# Load the Microsoft.Update.Session COM object
$UpdateSession = [Activator]::CreateInstance(
[Type]::GetTypeFromProgID("Microsoft.Update.Session")
)
$UpdateServiceManager = [Activator]::CreateInstance(
[Type]::GetTypeFromProgID("Microsoft.Update.ServiceManager")
)
# Add the scan package service
$UpdateService = $UpdateServiceManager.AddScanPackageService("Offline Sync Service", $ScanFile)
# Create an update searcher
$UpdateSearcher = $UpdateSession.CreateUpdateSearcher()
$UpdateSearcher.ServerSelection = 3
$UpdateSearcher.ServiceID = $UpdateService.ServiceID.ToString()
# Search for missing updates
$SearchResult = $UpdateSearcher.Search("IsInstalled=0")
# Display the list of missing updates
if ($SearchResult.Updates.Count -gt 0) {
$SearchResult.Updates
}
else {
Write-Host "No missing updates were found on this system."
}It can take a while for this code to run, especially if you have a slow Internet connection.
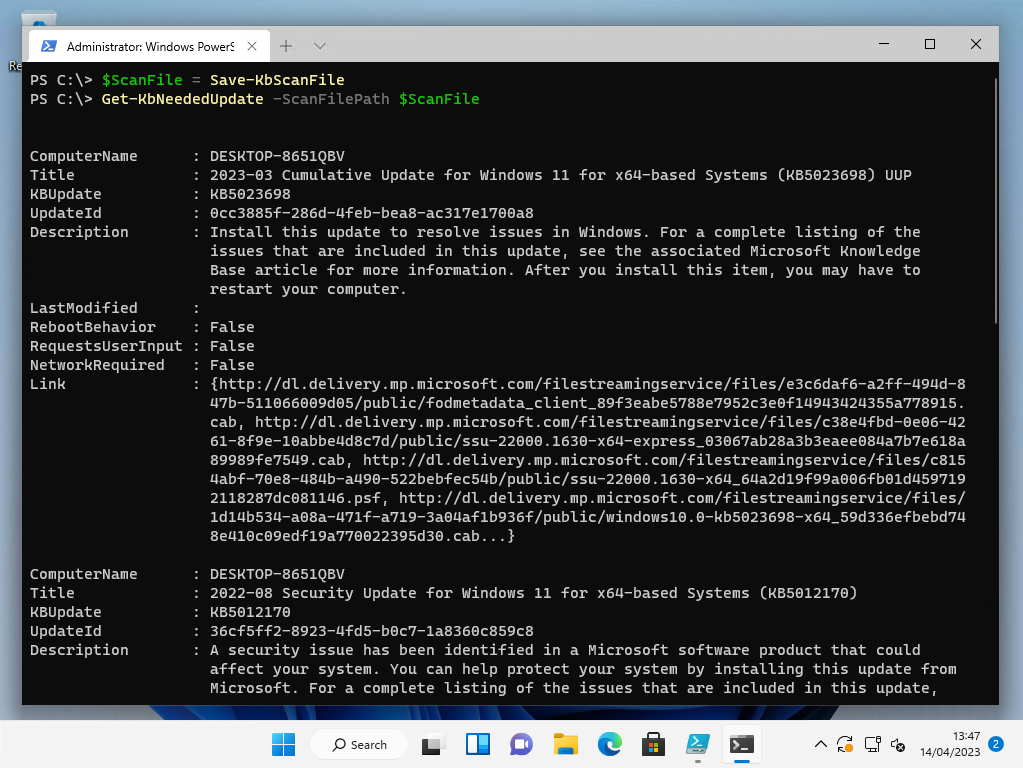
While the above is not a lot of code, it is unnecessarily long, especially when compared to how you could otherwise do it using the kbupdate PowerShell module:
$ScanFile = Save-KbScanFile
Get-KbNeededUpdate -ScanFilePath $ScanFile- Identify missing patches in a disconnected environment
- Provide a reality check on what products or categories you’re not syncing in your WSUS server or Configuration Manager Software Update Point (SUP)
Disconnected Environments
The 100% Compliance Lie
Beyond Operating System Patching
In this post, we discussed how to install the latest version of Windows updates using PowerShell. We focused on how to use the excellent Windows PowerShell module kbupdate, and also what it looks like to interact with the WUA API.
Remediating devices for missing Windows updates is only a small piece of the enormous battle that is cyber security. While the Operating System is a dominating piece of software on a device, accompanying third-party software is equally important and a significant risk if left unpatched.
More often than not, it is the most overlooked form of patching. As reported earlier by IBM, outdated third-party software leaves a device vulnerable as an attack vector used by hackers.
Products like Patch My PC can help you identify and remediate vulnerabilities from outdated third-party software on your devices by automating the packaging and integrating with Microsoft Configuration Manager, Intune, and WSUS.
Patch My PC offers features to scan your collected installed software inventory for both Configuration Manager and Intune. Coupled with excellent reporting, Patch My PC can help you keep on top of your patching strategy and ensure a better long-term security posture.
Resources
potatoqualitee/kbupdate: 🛡 KB Viewer, Saver, Installer and Uninstaller (github.com)
kbupdate – Scan and patch offline servers without WSUS – Chrissy LeMaire – YouTube
Using the Windows Update Agent API – Win32 apps | Microsoft Learn
Using WUA to Scan for Updates Offline – Win32 apps | Microsoft Learn
Searching, Downloading, and Installing Updates – Win32 apps | Microsoft Learn
Cost of a data breach 2022 | IBM – 3R8N1DZJ (ibm.com)
Set Up a Disconnected Network (Import and Export Updates) | Microsoft Learn
Synchronize updates with no Internet connection – Configuration Manager | Microsoft Learn